In the light of digital transformation, cloud computing has become widely adopted. The separation of ownership, management and usage rights of resources increases the possibility and severity of privacy risk in the cloud. How should enterprises consider privacy when deploying cloud products and services? The US National Institute of Standards and Technology (NIST) Privacy Framework1 is a risk-based tool used to manage privacy risk through governance and privacy engineering to evaluation. ISACA®also offers a set of tools such as the Microsoft Azure Audit Program, which sets audit objectives based on the NIST framework, and COBIT® 2019, which supplements the objectives in the NIST framework to manage risk.
Privacy Governance: Mapping COBIT 2019 With the NIST Privacy Framework
The NIST Privacy Framework provides privacy risk management implementation guidance. COBIT 2019, which includes change management and continual improvement management objectives, helps to implement sustainably (figure 1).
Figure 1—Step-by-Step Process for Privacy Risk Management

View Large Graphic
Source: (left) Adapted from the US National Institute of Standards and Technology (NIST), NIST Privacy Framework: A Tool for Improving Privacy Through Enterprise Risk Management, USA, 2020; (right) ISACA®, COBIT® 2019 Framework: Introduction and Methodology, USA, 2018
Step 1: Organizing Preparatory Resources
In figure 1, COBIT 2019’s 1st phase poses the question What are the drivers?
The drivers include stringent privacy and data protection regulatory demands, rising customer expectations and high-cost implications in terms of penalties from authorities for non-compliance, which result in legal enforcement and reputational harm. In the age of digital transformation, with the increased use of cloud computing—proliferation of data storage and usage in the cloud—cloud service providers (CSPs) may pose increasing privacy risk, especially in the areas of third-party risk management (TPRM) and dataflow management. For example, the collection and storage of historical sensitive data might be beyond the necessary and required retention period. The pain points/drivers in cloud computing are unauthorized data access, insufficient dataflow management and unnecessary or excessive retention of data.
Step 2: Determining Privacy Capabilities, Step 3: Defining Privacy Requirements, Step 4: Conducting Privacy Risk Assessments
As illustrated in figure 1, COBIT 2019’s 2nd through 5th phases ask Where are we now? Where do we want to be? What needs to be done? And, How do we get there?
Enterprises should begin by identifying their current activities and then consider how to adjust activities for their target profile, which indicates where they are now (COBIT 2019 phase 2) and where they want to be (COBIT 2019 phase 3) mapping. To address COBIT 2019’s phase 4 and 5 questions (What needs to be done? How do we get there?) enterprises should refer to the NIST Privacy Framework. The framework’s 5 functions define a streamlined way to analyze and articulate gaps, and its 18 categories can be mapped with the 5 domains in COBIT 2019. Together, they help describe the implementation steps to bridge the gaps (figure 2). Each function in the NIST Privacy Framework maps with one COBIT governance and management objective. The yellow dots in figure 2 highlight the applicable COBIT objectives to the privacy risk program in cloud.
Figure 2—Privacy Framework Cores Management

View Large Graphic
Source: (left) Adapted from the US National Institute of Standards and Technology (NIST), NIST Privacy Framework: A Tool for Improving Privacy Through Enterprise Risk Management, USA, 2020; (right) ISACA®, COBIT® 2019 Framework: Introduction and Methodology, USA, 2018
Step 5: Creating Privacy Requirements Traceability
COBIT 2019’s 6th phase, as shown in figure 1, asks How do we get there?
Evaluation of the enterprise’s privacy risk response should be ongoing to control, manage and report risk related to privacy risk management practices. The Microsoft Azure Audit Program assists enterprises in evaluating whether Azure services securely support operational and compliance objectives and provides an objective opinion on the adequacy and efficacy of the enterprise’s Azure implementation (figure 3).
Figure 3—Testing Steps
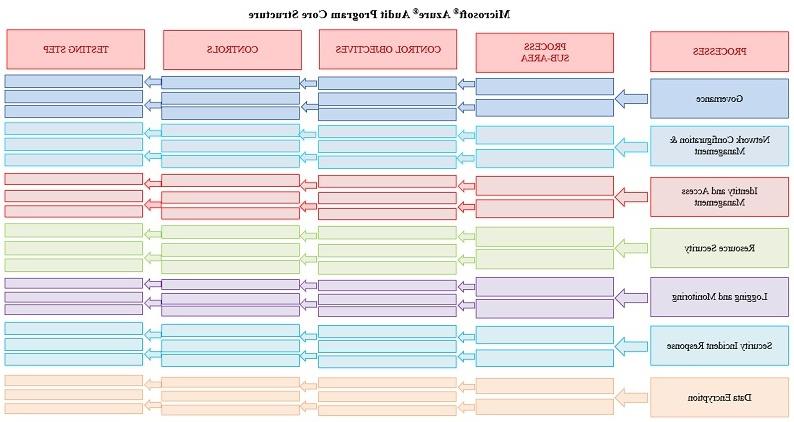
View Large Graphic
Source: Adapted from ISACA, Microsoft® Azure® Audit Program, 2020
After testing each control, the enterprise should evaluate the implementation by using either the NIST implementation tiers or the COBIT capability and maturity approach to manage performance (figure 4).
Figure 4—Performance Management Models

View Large Graphic
Source: (left) Adapted from the US National Institute of Standards and Technology (NIST), NIST Privacy Framework: A Tool for Improving Privacy Through Enterprise Risk Management, USA, 2020; (right) ISACA®, COBIT® 2019 Framework: Introduction and Methodology, USA, 2018
Step 6: Monitoring Change
Figure 1 shows that COBIT 2019’s 7th, and final, phase raises the question How do we keep the momentum going?
Ongoing monitoring of privacy risk changes is important to ensure that privacy governance is consistent with the enterprise’s current privacy policies and standards and aligned with the enterprise’s privacy risk governance goal. Azure Monitor logs are one of the useful tools that help enterprises using the Azure platform understand the overall security posture all within the context of IT operations, and at the same time, it sets a good example for other CSPs.
Hyperscaling Privacy Engineering in the Cloud
After building out a privacy governance program based on industry standards, that is, technical control frameworks (e.g., NIST Special Publication [SP] SP 800-53),2 risk frameworks (e.g., International Organization for Standardization [ISO] 31000),3 governance frameworks (e.g., NIST Cybersecurity4 and Privacy Frameworks) and data governance frameworks (e.g., ISO/International Electrotechnical Commission [IEC] 19944),5 the enterprise should identify the key technical controls. Next, the law and policy languages should be translated into engineering requirements. At the same time, cloud DevOps can be leveraged to automate perfunctory privacy actions and continuously monitor changes (i.e., identifying personal data through automated or manual tagging). Figure 5 describes how to take high-level privacy objectives and controls designed to protect against privacy infringement and translate them into meaningful, measurable and practical controls that privacy engineers can implement and monitor in order to address pain points: data access, dataflow management and data retention.
Figure 5—From Privacy Governance to Privacy Engineering

Conclusion
COBIT 2019, which includes useful guidance to facilitate a tailored implementation to ensure effective enterprise governance of information and technology, helps to effectively implement the NIST Privacy Framework to build a tailored privacy governance system, thus strengthening COBIT’s continuing role as an important driver of cloud computing in the age of digital transformation. The Microsoft Azure Audit Program provides evaluable control statements set as an example for enterprises to fit their respective environment and feasible technical requirements and step-by-step testing processes aimed intended to identify privacy risk and assists enterprises in making legal requirements tangible and practical for cloud engineering.
Andrea Tang, CIPP/E, ISO 27001 LA
Has a professional background in IT engineering and law. Currently, she works at Ernst & Young providing privacy consulting services. Previously, she worked for Oracle Cloud Infrastructure as an IT developer. Tang has published professional articles in the ISACA® Journal and contributed to the guidebook released by the ISACA® China Technical Committee. As an active volunteer in the ISACA China Chapter, she was the winner of the Outstanding Young Professional Award in 2018-2019.
Endnotes
1 National Institute of Standards and Technology (NIST), NIST Privacy Framework: A Tool for Improving Privacy Through Enterprise Risk Management, USA, 16 January 2020
2 National Institute of Standards and Technology, Security and Privacy Controls for Federal Information Systems and Organizations, USA, April 2013
3 International Organization for Standardization (ISO), ISO 31000 Risk Management, Switzerland, 2018
4 National Institute of Standards and Technology, Cybersecurity Framework, USA, 2018
5 ISO/International Electrotechnical Commission (IEC), ISO/IEC 19944 Information Technology—Cloud Computing—Cloud Services And Devices: Data Flow, Data Categories And Data Use, Switzerland, 2017
